A decade ago, the idea of working from home was nowhere near as prevalent as it is today. For most companies, remote working was not possible, either due to limitations in technology or company culture. COVID-19 has forced companies all over the world to adapt and embrace remote work - at least in the short-term. Although adapting to working from home has been a fast and furious journey for lots of organisations, many companies are now figuring out that new ways of working, supported by the mobile workspace, have considerable long-term benefits.
Mobile workspace is an environment where staff can connect to the company network and access the usual voice, apps and data systems remotely and securely. This method of working isn't tied to a physical location and staff can use smartphones, tablets, laptops and notebooks depending on company policy, for work. Many companies are deploying or have already deployed VPN solutions and other remote access technologies to allow mobile workers to connect to on-premises infrastructure, so that they can access corporate resources remotely over internet. This offers great business benefits – but it also presents new risks that can be concerning for the CISOs, CSOs and Security Officers.
What are the risks?
Mobile working and remote access extend the transit and storage of information outside of a company IT infrastructure, typically over the internet. Organisations with impromptu or traditional systems are most vulnerable to the following risks:
- Mobile devices are easily lost or stolen, which can lead to access of sensitive information or systems.
- Users working in public spaces are vulnerable to being observed and overlooked, which can potentially compromise authentication credentials.
- User credentials stored with a device, such as a token for remote access, could be lost or stolen. This can lead to the compromise of services or information stored on or accessible from that device.
- An attacker may attempt to install malicious software or hardware if a device is left unattended. This may allow the attacker to monitor all user activity on the device, including authentication credentials.
How to mitigate risk
Microsoft’s unique perspective on enterprise security in the mobile-first, cloud-first world provides significant benefits to every organisation, regardless of its size, and allows businesses to handle any kind of security threat. Microsoft 365 Threat Protection service provides a one-stop solution for organisations to detect and investigate advanced threats, compromised identities, and malicious actions across on-premises and cloud environments. It is a unified pre and post-breach enterprise defence suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks. Threat Protection capabilities are integrated by default in Microsoft 365.
With Microsoft Threat Protection solution, security professionals can stitch together the threat signals that each of these products receive and determine the full scope and impact of the threat; how it entered the environment, what has been affected, and how it's currently impacting the organisation. Microsoft Threat Protection takes automatic action to prevent or stop the attack and self-heal affected mailboxes, endpoints, and user identities. The following diagram depicts the threat protection services and capabilities in Microsoft 365.
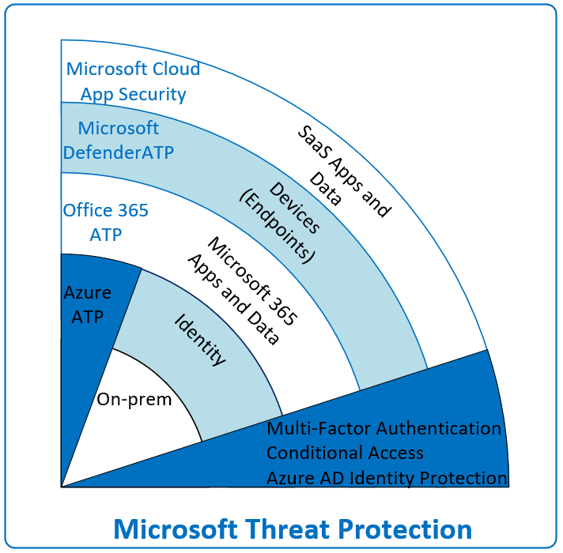
Azure multi-factor authentication: Multi-factor authentication is a way of proving that a user is who they say they are when signing in. The three most common kinds of factors are: something you know, like a password or pin; something you have, like a smartphone or secure USB key; something you are, like a fingerprint or facial recognition. With multi-factor authentication enabled your identity is secured, even if someone tries to sign in using your username and password, because they can't provide the second factor. MFA provides the foundation of securing an on-premises, cloud or hybrid environment and is aligned with the principle of Zero Trust security; “never trust and always verify”. Every access request is fully authenticated and authorised before granting access.
Azure AD Conditional Access: Azure AD Conditional Access brings identity login signals together to make decisions and enforce organisational policies. It is the security foundation of new identity-driven control plane based on “if-then” statements.
Azure AD Identity Protection: Azure AD Identity Protection is an automated risk detection and remediation tool of identity-based risks including suspicious actions related to user accounts, such as login from an anonymous IP address, The risk signal triggers remediation efforts, such as requiring users to perform MFA.
Azure Advanced Threat Protection (Azure ATP): Azure ATP is a cloud-based security solution that leverages on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed to organization. It identifies anomalies with adaptive built-in intelligence to give administrators insight into suspicious activities and events.
Office 365 Advanced Threat Protection (Office 365 ATP): Microsoft Office 365 Advanced Threat Protection is a cloud-based email filtering service that helps protect organisations against unknown malware and viruses by providing robust zero-day protection and includes features to safeguard organisations from harmful links in real time.
Microsoft Defender Advanced Threat Protection (MDATP): Microsoft Defender ATP uses the combination of endpoint behavioural sensors, cloud security analytics and threat intelligence to detect sophisticated threats, providing cloud-delivered protection for near-instant detection and blocking of new and emerging threats.
Microsoft Cloud App Security (MCAS): Microsoft Cloud App Security provides rich visibility, control over data travel and sophisticated analytics to identify and combat cyberthreats across all Microsoft and third-party cloud services.
Use cases and business scenarios
On-premises infrastructure - If your organisation’s apps and infrastructure are still on-premises, you can utilise Microsoft 365 Threat Protection service to protect your environment and enable secure access for remote workers.
- Step 1. Sync your on-premises Identity to Azure Active Directory using Azure AD Connect lightweight application.
- Step 2. Enable combined security information registration that will give users best experience and register them for self-service password reset.
- Step 3. Enable MFA for all users using conditional access policy. This one simple step will prevent 99.9 percent of attacks on your organization accounts.
- Step 4. Enforce MFA on VPNs using conditional access in addition to all your apps.
- Step 5. Enable Hybrid Modern Authentication to secure on-premises skype for Business and Exchange Servers.
- Step 6. Implement hybrid Azure AD Join using Azure AD Connect. This will join your on-premises domain joined devices to Azure AD. You can then apply device based conditional access policy that only let users access your environment from these trusted devices.
- Step 7. Deploy Azure ATP to identifies anomalies with adaptive built-in intelligence, giving administrator insights into suspicious activities and events.
- Step 8. Deploy Microsoft Defender Advanced Threat Protection to secure endpoint and integrate with Azure ATP.
Hybrid or cloud-only infrastructure - You have already started your cloud journey and are using hybrid or cloud-only identity. Your apps and infrastructure are already extended to or hosted in the cloud, but you might be unsure how to protect data and enable secure access for your remote users.
- Step 1. Enable MFA using Conditional Access policy if you haven't already.
- Step 2. Implement Azure AD Identity Protection to secure identity.
- Step 3. Implement Azure ATP to identify anomalies with adaptive built-in intelligence.
- Step 4. Deploy security and compliance using Office 365 ATP to secure your apps and data from attack. DLP policy will prevent inappropriate sharing of data.
- Step 5. Deploy Microsoft Defender Advanced Threat Protection to secure endpoint and integrate with Azure ATP, Office 365 ATP, Cloud App security and Azure information Protection.
- Step 6. Enable Microsoft Cloud App security and connect to office 365, other third-party apps and integrate with Microsoft information protection.
Next steps
Depending on your current environment and security policy these steps might vary, but regardless of your current IT infrastructure you can start taking advantage of Microsoft M365 enterprise class security today to protect your organisation and provide remote workers with seamless and secure access to all on-premises and cloud-based applications. Contact Core to find out how we can help you deploy Microsoft’s security features to protect your remote working environment.







