Cloud-based remote working has enabled organisations to achieve continuity in a difficult time. However, this has shone an even greater light on two longstanding questions.
- How do I secure my cloud services in multi-domain, remote working world?
- How do I achieve a balance between an effective security strategy and a productive user experience?
Previously, organisations locked down access to their Microsoft and other cloud applications so that any attempt to gain access from an external location or unrecognised device was blocked.
While somewhat effective if access to a site or corporate device is available, this approach neither prepares for scenarios where choice of location and device is not available, nor fully embraces the flexibility and productivity available with cloud computing.
However, the fear of opening up assets and data to external access from remote locations and non-corporate devices is an understandable one.
An answer to this concern, as well as the two questions posed at the beginning of this article, is conditional access.
Conditional Access
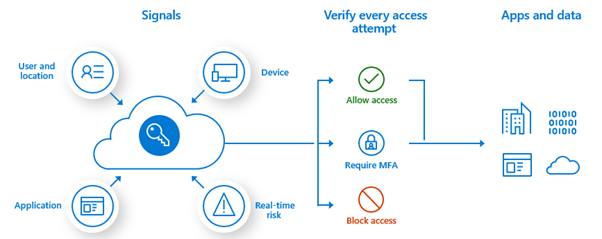
Conditional access sits within Microsoft’s Azure Active Directory to enforce policies against signals being sent and received, thereby granting or denying access to different applications, resources and services.
For example, if the Head of Finance wants access to Payroll, conditional access can be used to create a policy requiring an associated action be performed before access is permitted.
This is termed an ‘If-Then’ relationship. ‘If a user wants access to payroll, then they must complete Multi Factor Authentication (MFA)’. Conditional access can be far more complex and granular than this, however.
Using a range of available criteria, including the user, device or sensitivity of the access request, conditional access can be used to apply the right level of control at the right time to ensure you secure your assets, while not hindering your users unnecessarily.
Common signals which conditional access considers include:
- User/ Group Membership
- IP Location
- Device basis
- Application basis
- Real time risk calculation and detection
- Microsoft Cloud App Security
Having considered the signal, you must also consider the access controls which must be satisfied before a user is allowed access. For example:
- Complete Multi-Factor Authentication
- Require device to be marked as compliant
- Require Hybrid Azure AD joined device
- Require approved client application
While conditional access is a Microsoft tool within Azure Active Directory, its reach extends far beyond Microsoft cloud applications with the same level of functionality available.
Users will leverage more than 1000 cloud applications in the course of their work. In order to secure these applications, it is essential that your cloud security strategy can manage and monitor them.
Thousands of cloud applications are pre-Integrated into Azure AD. This means that any cloud application which is integrated to your Azure AD tenant can have conditional access policies applied to them and can also leverage single sign-on to the application with the users Azure AD account.
In a world where users are interacting with a range of ever-changing cloud applications and doing so across devices and locations, it is essential that access to these applications is managed through an integrated platform that delivers a seamless user experience that is also secure.
However, it is also essential that configuration of these policies is proportionate to the sensitivity of the application, resource and data.
Other applications, including those which are on-premise or custom, can be integrated to Azure AD and make use of Conditional Access and Single Sign On. The granularity available for access to these applications means all cloud applications are secured and monitored.
Extensions of Conditional Access
Conditional access can also be used in tandem with Intune or Microsoft Cloud App Security (MCAS), to add further functionality including mobile device management, mobile application management and Cloud Access Security Broker.
Intune
Intune is Microsoft’s cloud-based device management solution. Intune enhances the capability of conditional access by enabling Mobile Device Management and Mobile Application Management, further protecting corporate data and services being accessed through both Corporate Devices and Bring Your Own Device (BYOD).
Devices can be registered with Intune to give your organisation complete control of the device, its settings and security. This is usually the case for corporate devices.
For personal devices, this may not be possible or appropriate, so you can instead set policies based around specific applications, allowing users to keep control of their personal device and personal data, while Intune facilitates control over organisation data.
This could be by restricting the actions a user can take (i.e. Save, Copy and Paste), enforcing certain settings for that application and enabling a remote wipe of selective data, removing organisation data from applications without impacting the personal data on the device.
The applications being used to access data can also be subject to conditional access controls in Intune, such as limiting access to emails to a certain application only. E.g. Only allowing Outlook to access Exchange Online.
You can also restrict access to Office 365 applications to the browser only, so mobile applications are not permitted access. If you do allow access to applications on mobiles, you can require additional information to access the apps, such as PIN or biometric. These can also be different to those used to unlock or access the device itself, adding an additional layer of security if the mobile devices primary password or PIN credentials are compromised or shared.
Microsoft Cloud App Security (MCAS) – Conditional Access App Control
Microsoft Cloud App Security (MCAS) is a Cloud Access Security Broker that sits between users and cloud applications, monitoring activities, enforcing policies and remediating threats.
MCAS provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your Microsoft and third-party cloud services.
In the context of conditional access, MCAS has Conditional Access App Control to enable real time visibility and control over access and sessions within your cloud applications, by setting access and session-based policies.
Through this you can:
- Avoid data leaks by blocking downloads before they happen
- Set rules that force data stored in and downloaded from the cloud to be protected with encryption
- Gain visibility into unprotected endpoints so you can monitor what's being done on unmanaged devices
- Control access from non-corporate networks or risky IP addresses
MCAS utilises a reverse proxy setup, which means traffic to and from your cloud applications is routed through MCAS, providing greater control and visibility over the sessions and access in all your cloud applications.
For example, you could set-up a conditional access policy, which stipulates that access to your cloud applications must pass through MCAS to be allowed.
Any application which can be integrated to the authentication protocols in Azure AD can also integrate with MCAS and can have session and access controls applied.
Requirements
There are several requirements for Conditional Access, as well as for Intune and Microsoft Cloud Application Security:
- Conditional Access is part of Azure AD Premium P1 License, which is a part of EMS E3
- All users targeted or subject to conditional access policy will need to be covered by a license which includes Azure AD Premium P1 features
- A working Azure Active Directory tenant
- Intune is available as a standalone license, or as a part of EMS E3
- Microsoft Cloud App Security can be licensed in several ways, including some features available in limited scope across some licenses:
- Microsoft 365 E5
- Microsoft 365 E5 Security
- Microsoft 365 E5 Compliance
- EMS E5
- EMS E3 + Microsoft Cloud App Security Bundle
- Microsoft Cloud App Security Standalone